Web API credentials
For API requests that require authorization, it is necessary to add the relevant credentials to Credential Manager.
-
Select System > Security > Credentials and click New.
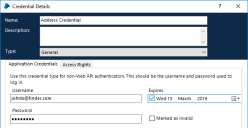
The Credentials Details dialog displays.
-
Select the authentication type for the credential:
- General – Add the authentication username and password required to create credentials for non Web-API authentication.
- Basic – Add the authentication username and password required to create the basic authentication header.
- Bearer Token – Add the Bearer token to add to the authentication header.
- OAuth 2.0 (Client Credentials) – Add the client identifier and secret, stored in a credential, to retrieve an OAuth 2.0 access token from an authorization server. The access token is then used to authenticate Web API requests.
- OAuth 2.0 (JWT Bearer Token) – Add the JWT issuer and private key, used to sign the JWT – a PKCS8 private key is expected in a PEM base64-encoded format. The JWT is then sent to the authorization server to get the access token required to authenticate the request.
If the selected authentication type requires a username and password, HTTP password authentication protocol dictates that passwords can only contain any of the first 128 ASCII characters. If any other characters are used, Blue Prism replaces the character with ? resulting in a failed login attempt.
- In the Additional Properties section, add any general purpose, named properties for the credential. The values are held securely within the database and can be requested by processes.
-
Select the Access Rights tab and define the required permissions.
It is recommended that the access rights are configured so only user accounts with the appropriate security roles are able to access to each credential. When a credential is limited by security role:
- The selected security roles must be held by the user(s) who require access to the credential when building or debugging a process or object.
- Only runtime resources that are configured to explicitly authenticate will potentially be able to access the credential.
- The selected security roles must be held by the account(s) used by runtime resources to authenticate against the environment.
- Click OK to save the credential.
For further information about configuring authentication types in API definitions, see Common authentication.
 Docs
Docs